Due to business disruption caused by data breaches, companies may find that they violated one or more of their bank covenants at the balance sheet date. As a result, executives will have to plead with their lenders for a waiver to cure the violation(s) and hope the lenders do not call the debt. As the lenders evaluate the probability of repayment and future infractions, an agreement may hinge on more restrictive covenants and an increased cost of capital.
This article discusses the cost of capital, capital budgeting, calculating the cost of money, and breach. So before we dive into the cost of capital, let’s quickly define a data breach.
What is a Data Breach?
Data is an asset, depending upon the value assigned to the information. What is the loss or consequence to the business and team when the data is stolen or inaccessible? When criminal attackers gain access to the data systems, their actions create loss events.
A data breach is a security violation in which sensitive, protected, or confidential data is copied, transmitted, viewed, stolen, or used by an unauthorized individual. This type of unsystematic risk affects company cash flows.
With this point made, let’s move forward.
 Unsure + insecure is purposeless in lowering your cost of capital.
Unsure + insecure is purposeless in lowering your cost of capital.What is the Cost of Capital?
According to Corporate Finance Institute, the cost of capital is the minimum rate of return that a business must earn before generating value. Before a company can turn a profit, it must generate income to cover the cost of the capital it uses to fund its operations.
The structure consists of the cost of debt and equity used to finance a business. The actual cost of capital depends on its capital structure. The company may rely either solely on equity or debt or use a combination of the two.
Importance of Cost of Capital in Capital Budgeting
In the case of expansion, the cost of capital is the minimum return necessary to justify undertaking a capital budgeting project, such as building a new facility.
Another consideration for capital budgeting is implementing controls, incident response, and recovery measures to limit lost revenue from operational outages. Let us not forget the wages paid to workers when disrupted processes impede staff productivity during the blackout.
Analysts and investors use the term cost of capital to evaluate whether the cost justification warrants a decision to proceed. Investors may use the term to assess the potential return of a given investment with its cost and risks.
We also use the cost of capital as the discount rate for the company’s free cash flows.
How to Calculate Cost of Capital?
According to the Association of International Certified Professional Accounts (AICPA), the most common approach to calculating the cost of capital is to use the Weighted Average Cost of Capital (WACC). The WACC is the average cost of the organization’s finance (equity, bonds, bank loans, and preference shares) weighted according to each element’s proportion to the total pool of funds.
The WACC is derived by first estimating the cost of each source of finance separately (e.g., ordinary shares, debt, preference shares) and then taking a weighted average of these individual costs, using the following formula:
- Step 1: Calculate weights for each source of capital.
- Step 2: Estimate the cost of each source of capital.
- Step 3: Multiply the proportion of each source of capital by the cost of that source of funds.
- Step 4: Sum the results of step 3 to give the weighted average cost of capital.
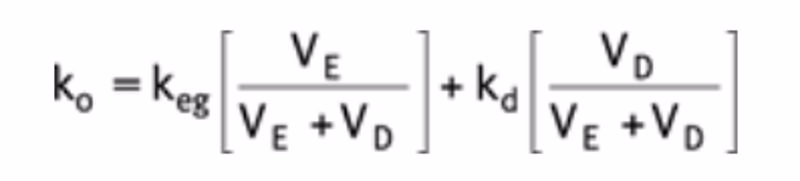
The existing WACC of an entity should only be used as a discount rate for a new project if the business risk and the capital structure (financial risk) are likely to stay constant. One sharp distinction, WACC is intended for substantial new investments. If the new funding is marginal to the company, WACC would not be used as a discount rate when using net present value (NPV) or internal rate of return (IRR) calculations.
Suppose the business risk of the new project differs from the entity’s existing business risk. In that case, apply a risk-adjusted WACC by recalculating the cost of equity to reflect the business risk of the new project. This process involves the technique of degearing and regearing beta factors.
If the team expects the capital structure (financial risk) to change slightly when the new project launches, you should recalculate the WACC using the new capital structure weightings. This method is appropriate when the change in capital structure is not significant or when the team treats the new project as a new business with its long-term gearing level.
Finally, use the project appraisal’s Adjusted Present Value (APV) method when the capital structure is probable to change significantly. This approach separates the investment element of the decision from the financing element and appraises the aspects independently. When there are complex funding arrangements, such as subsidized loans, APV is put forward.
U.S. industry benchmarks can help estimate your cost of capital. Duff & Phelps offers an online platform to aid your valuation analysis, with data available for download back to 1999.
Impact of Cost of Capital
Earlier, we shared that data is an asset. If your business relies upon data-based workflows to operate, criminals have an opportunity to monetize your weaknesses. Whether intellectual property, recipes, drawings, cost data, or customers, you value this data.
Recovering from data breaches costs money, and your current cash flow may not absorb the expenditures. Debt is a cheaper source of financing than equity until you have too much debt or violate covenants with your lenders.
Depending upon your teams’ ability to resist attacks, you must recover quickly with minimal data loss. In this case, the average cost of capital may remain unchanged. However, many companies discover during loss events that they have not prepared for this level of proficiency.
Based upon incident reports and insurance data, the frequency and severity of attacks continue to increase. For organizations that experience a significant system breach, operating profit levels decline during and after the data breach. The long tail of increased expenses can last for several periods or quarters depending upon incident response and recovery efforts.
What happens when your entire business has an unplanned shutdown? We also need to account for this extended loss event’s impact on other stakeholders, such as our customers, suppliers, vendors, and lenders.
The magnitude of one incident could trigger contractual fines, stakeholder monetary loss, legal costs, lost market share, diminished stock price, and increased cost of capital.
 A protection strategy is essential to making future cash flow disruptions less painful.
A protection strategy is essential to making future cash flow disruptions less painful.Why is data protection significant?
Intangible assets such as data are the predominant source of economic value for many businesses. Understanding how variables in data access impact processes and the cumulative effect for cash flow generating workflows highlights sensitivities for decision-makers.
The likelihood of workflow failures increases as your resilience diminishes. The lack of understanding and funding undermines action to contain cyber risk. Will you invest in identifying disruption before it happens or spend more money during the data breach and after recovery?
Sustainability is imperative in manufacturing, and the call to action is compelling. From cost and waste reduction to improving workforce performance, cyber risk strategy management and executive stewardship benefits are significant for manufacturers of all sizes and sectors.
In life and business, trust is essential, as are clear mutual expectations. When you commit to your customers and vendors, you provide assurances that you will deliver. Likewise, when your business needs to borrow, you must trust your lender as the lender evaluates your ability to repay your loan and sets your cost of capital.
Planning and Budgeting
Developing a multi-pronged strategy is essential to making future cash flow disruptions less painful, but finding the right balance of technology and policy-based controls can be difficult. The uncertainty of future business and cash flow disruption requires evaluation. That’s where Certitude Security can help.
We utilize a multi-stakeholder shared purpose approach to streamline team effectiveness. Once business and IT management know that we focus on helping the team and not displacing them or harming their reputation, output improves. Shared understanding is a force multiplier that allows for higher-value conversations, information exchange, and actionable insights.
As a proud supporter of American companies, Certitude Security® is working diligently to inform leaders and facilitate essential asset protection priorities for manufacturers and supply chains throughout the United States.
Problem discussions can be a defining moment in your career. If you are interested in value creation, learn about SPOT-Beam™ by Certitude Security®. We look forward to helping you and your business succeed!

